The advent of 5G technology promises unprecedented speeds and connectivity, but at what cost to our environment? This article delves into the nuances of 5G’s impact on the carbon footprint, providing a balanced view on whether this technological leap forwards is a friend or foe to our planet. The Evolution of Wireless Technology From the
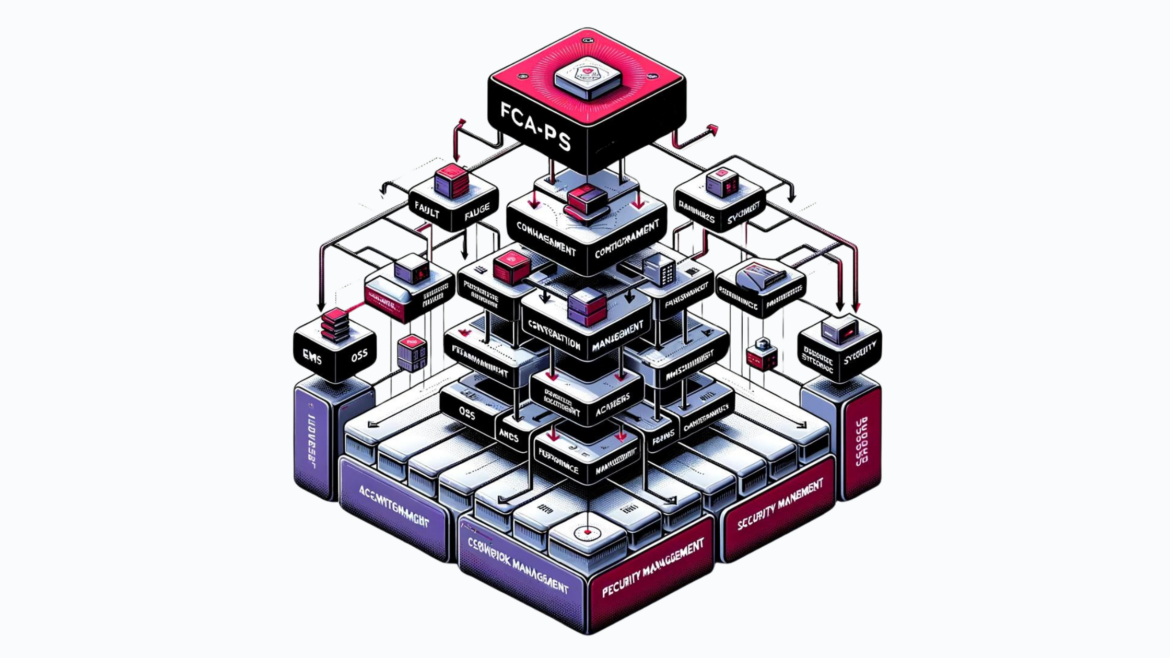
In the intricate landscape of telecommunications, understanding the various systems and frameworks that ensure seamless network operations and service delivery is crucial. This blog delves into Operational Support Systems (OSS), Element Management Systems (EMS), Network Management Systems (NMS), Business Support Systems (BSS), and the pivotal role of the FCAPS model in network management. Operational Support
In the digital era, the efficiency of network resource management is paramount for businesses to thrive. The distinction between managing network resources and other inventories is crucial for optimizing operations and ensuring network reliability. This comprehensive guide delves into the nuances of network resource inventory, contrasting it with the management of other organizational assets, and
5G stands for Fifth Generation Wireless technology, marking a monumental leap in the evolution of cellular networks. Building on its predecessors – GSM (2G), CDMA (3G), and LTE/LTE-Advanced (4G) – 5G is set to revolutionize how we interact with the digital world. The technology is codified in the 3GPP NR (New Radio) specifications and operates
In an era where sustainability and efficiency are not just goals but necessities, SYNERGY emerges as a transformative solution for smart energy management. Whether you’re overseeing a sprawling industrial complex or managing a cozy smart home, understanding, and controlling your energy consumption is pivotal. SYNERGY doesn’t just promise; it delivers. Here’s a deep dive
The effectiveness of Operational Support Systems (OSS), Network Management Systems (NMS), and Element Management Systems (EMS) is fundamentally tied to how accurately these systems reflect the real-time status of the network they manage. The primary goal of these systems is to provide a comprehensive, up-to-date view of the network’s operational state, including its configuration, performance,
In the digital era, the efficiency of network resource management is paramount for businesses to thrive. The distinction between managing network resources and other inventories is crucial for optimizing operations and ensuring network reliability. This comprehensive guide delves into the nuances of network resource inventory, contrasting it with the management of other organizational assets, and
In the intricate world of Wi-Fi networking, the ability to effectively manage bandwidth is not just beneficial—it’s essential. The introduction of GEMS (Global Enterprise Management System) into this ecosystem marks a significant leap forward. This powerful network analysis tool is adept at enhancing the monitoring and optimization of Wi-Fi networks across the 2.4 GHz, 5
The evolution of mobile networks, particularly with the introduction of LTE and 5G, has brought about a paradigm shift in how we perceive and utilize bandwidth. The crux of this transformation lies in the intricate interplay between frequency bands, channel bandwidth, and spectral efficiency. Let’s delve deeper into these concepts and unravel how they collectively
In the digital age, bandwidth is the lifeblood of network communication. Whether you’re streaming your favorite show, attending a video conference, or managing a data-intensive project, understanding, calculating, and optimizing your bandwidth is crucial. Let’s dive into the nuances of bandwidth calculation and explore strategies for optimization and monitoring to ensure a smooth digital experience.
Top News
The “Satellite Services Consultancy Agreement” between #Türksat A.Ş AND TTG International was signed by Dr. Selman Demirel, Deputy General Manager of Satellite Services, and Emine Beyaz, CEO of TTG International,
The “Satellite Services Consultancy Agreement” between #Türksat A.Ş AND TTG International was signed by Dr. Selman Demirel, Deputy General Manager of Satellite Services, and Emine Beyaz, CEO of TTG International, ...According to the results of the research, TTG Int. once again has been among the Turkey 2021 Top 500 IT companies.
TTG International is a company that provides its clients with advanced technology solutions to help them grow their business. They have been recognized as one of the top 500 IT companies in Turkey and are proud to be among the future-oriented companies driving innovation in Turkey. ...AR-GE 250
TTG International LTD has once again proved its research and developer spirit in genetics by taking part in two major research conducted throughout Turkey within the scope of its R&D studies in the field of telecommunications and IT management software (OSS) and its 2021 activities. According to the research prepared by Turkishtime on &#...Türk Telekom’dan yerli şebeke gözlem platformu
Haberleşme Teknolojileri Kümelenmesi (HTK) firmalarından TTG International’ın, Türk Telekom mühendislerinin de desteğiyle geliştirdiği GEMS-FAMAN platformu, Türk Telekom şebekesinde ticari olarak kullanılmaya başlandı İSTANBUL (AA) – Türk Telekom, müşterilerine yüksek performanslı şebeke servisleri sunmak üzere GEMS-FAMAN Platformu̵...