Network configuration compliance is the process of ensuring that your network’s controls, policies, and device configurations align with the latest industry standards, such as HIPAA and PCI DSS. It’s about fortifying your network against potential threats and meeting regulatory demands.
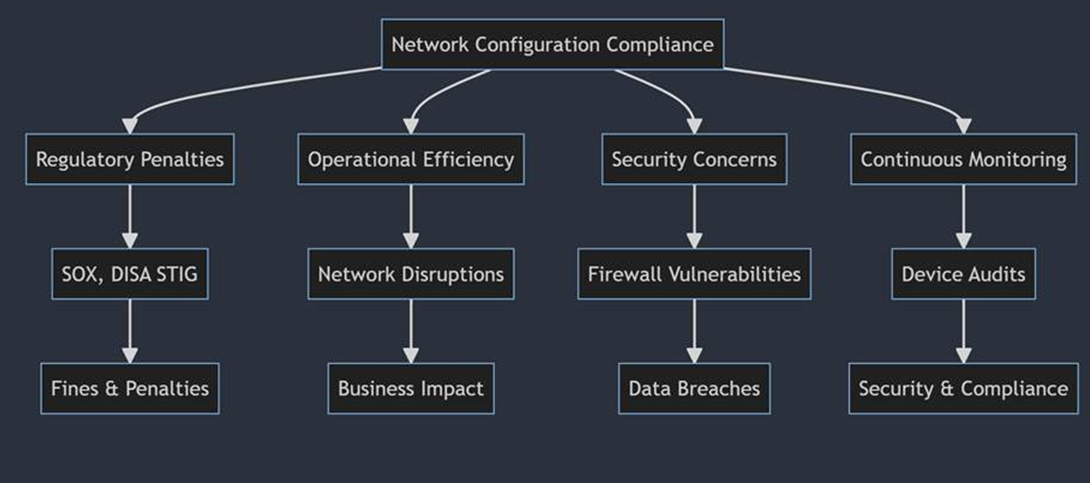
The Importance of Network Configuration Compliance
- Regulatory Penalties: Non-compliance can result in substantial fines from regulatory bodies or governments for not adhering to standards like SOX or DISA STIG.
- Operational Efficiency: Misconfigured devices can cause network disruptions, especially during high traffic periods, impacting business operations and revenues.
- Security Concerns: Minor alterations in configurations, especially in firewalls, can expose the network to cyber threats, leading to potential data breaches.
- Continuous Monitoring: With the ever-evolving industry regulations, it’s crucial to regularly audit device configurations, software updates, and hardware components to ensure security and compliance.
Strategies for Achieving Compliance
- Automated Configuration Management: Utilize automated tools to quickly audit device settings and security policies. These tools can detect unauthorized changes, streamline the configuration process, and enhance overall network security.
- Proactive Monitoring: Employ network administration tools to monitor configuration settings, data security policies, and network traffic. Regular network assessments can help identify and address potential vulnerabilities.
- Documentation: Maintain detailed records of data security measures, device configurations, and system maintenance procedures. This not only enhances security but also ensures you’re always audit-ready.
Spotting Non-compliant Configurations
Relying on manual methods to track non-compliant configurations can be tedious and error-prone. Automated tools offer a more efficient approach. Advanced configuration management software allows you to establish configuration baselines, which serve as a reference point for optimal device settings. Any deviations from this baseline can be quickly identified and rectified.
Key Compliance Standards to Consider
- DISA STIG: Developed by the Defense Information Systems Agency (DISA), these guidelines help the Department of Defense (DoD) bolster its IT infrastructure against external threats.
- NIST FISMA: Overseen by the National Institute of Standards and Technology (NIST), these guidelines mandate state and federal agencies to implement stringent security controls.
- HIPAA: This regulation necessitates organizations to protect sensitive health information through encryption, password protection, and other security measures.
- PCI DSS: A global standard that mandates businesses to securely handle financial information.
- GDPR: An EU regulation that requires organizations to maintain transparency when processing personal data of EU citizens.
TTG’s GEMS (Global Enterprise Management Solutions) is a game-changer for configuration compliance as renowned tool designed to streamline various aspects of network management;
Centralized Management: GEMS provides a centralized platform to manage and monitor all your network devices, ensuring that they adhere to the required compliance standards.
- Real-time Monitoring: With GEMS, businesses can enjoy real-time monitoring of their network configurations, ensuring immediate detection of any deviations or unauthorized changes.
- Automated Compliance Checks: GEMS can automate the process of checking device configurations against compliance standards, reducing the manual effort and minimizing human errors.
- Detailed Reporting: GEMS offers comprehensive reports that detail the compliance status of network devices, making it easier for IT teams to identify and rectify any non-compliant configurations.
- Integration with Industry Standards: GEMS is designed to integrate seamlessly with various industry standards, ensuring that your network is always in line with the latest regulatory requirements.
- Enhanced Security: Apart from compliance management, GEMS also offers robust security features that protect your network from potential threats and cyberattacks.
Incorporating GEMS into your network management strategy can significantly simplify the process of achieving and maintaining network configuration compliance. Its advanced features and user-friendly interface make it an invaluable tool for businesses aiming to fortify their networks and meet regulatory demands.




