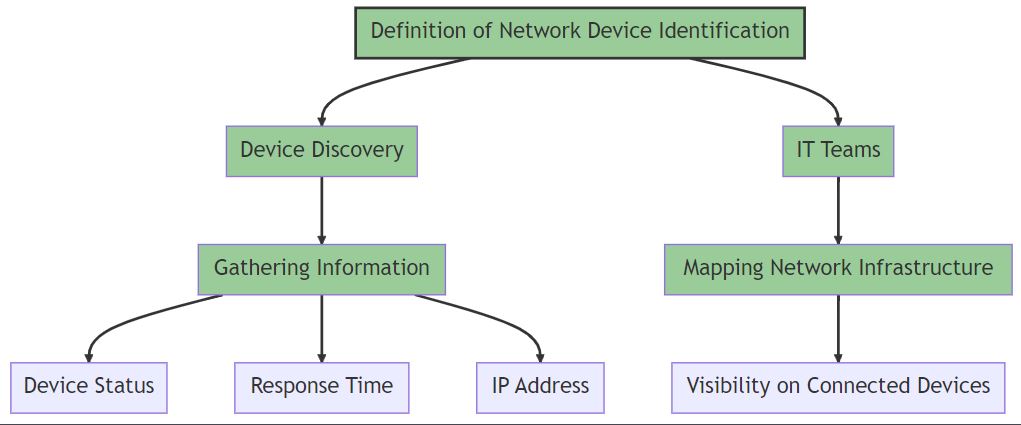
Network device identification, often referred to as device discovery, involves locating network hardware and collecting comprehensive data about them, including their status, response time, and IP address. This process is usually the initial step taken by IT professionals when they aim to map and oversee their network infrastructure, ensuring they have a clear perspective on all connected devices.
How to Manually Detect Unknown Devices on a Network?
To pinpoint an “unidentified device on a network,” one can utilize the command-line interface (CLI) of their computer. Different operating systems, be it Windows, Linux, or macOS, offer unique networking commands like “ipconfig” and “ping” for elementary network scanning and diagnostics. Recognizing network devices also necessitates a grasp of how IP addresses are allocated. Every device in a network needs a distinct IP address for communication, which can either be assigned dynamically by a DHCP server or set manually.
Here’s a guide to help you detect network devices:
- Launch the Command prompt or Terminal based on your OS – Windows, Linux, or macOS.
- Retrieve network configurations, such as the default gateway and IP address, using the command prompt.
- Windows users: Input “ipconfig” and press enter. This reveals the sub-net mask, default gateway, and your computer’s IPv4 address.
- For Linux and macOS users: Use the “ifconfig” command to access all network configurations.
- Execute the “arp -a” command to see all IP addresses linked to your network, showcasing the MAC address and the type of allocation (static or dynamic) for each device.
- Enter “nslookup” followed by any IP address from the “arp” command. This reveals the host-name of the specified IP address or any unidentified device in the network.
Automated Detection of Unknown Devices on a Network: Manually pinpointing devices and their corresponding IP addresses in expansive or diverse networks can be a daunting task for IT departments.
Network discovery applications autonomously scan and track network devices, keeping an up-to-date equipment inventory. This proves invaluable for organizations seeking swift ways to detect devices on their network. Such software allows for rapid tracking of IP and MAC addresses, connection velocities, and port specifics of all linked devices. They employ various discovery protocols, including SNMP, LLDP, and CDP, to extract in-depth device data. Moreover, these tools utilize ping sweeps to ascertain the active status of network hardware. Non-responsive devices to ICMP echo requests are labeled as inactive.
Contemporary network discovery applications also offer visual tools to assess both logical and physical connections of your devices using evolving network diagrams. These visual aids can identify unfamiliar devices and any alterations in the network structure. For instance, unauthorized connections by a breached device can be detected and subsequently blocked using network mapping. Advanced scanning tools also facilitate in-depth traffic analysis, helping pinpoint network lags, unusual traffic patterns, and potential security threats.
Manually Identifying Devices on a Wireless Network: One approach to detect devices in wireless networks is by accessing the router’s web interface. However, this method might not offer intricate details about network devices, such as data transfer rates or packet losses. Typically, each device in a wireless setup possesses a unique IP and MAC address, assigned by routers via the DHCP protocol.
Here’s a guide to detect devices using the router’s web portal:
- Launch a web browser and input the router’s internal IP address in the address bar. To determine the IP address:
- Windows users: Navigate to the taskbar, open the Command prompt utility, type “ipconfig”, and press enter. The router’s IP address will be displayed under the Default Gateway.
- macOS users: Click on the Wi-Fi icon in the menu bar, choose Open Network Preferences, then select Advanced Settings. In the subsequent window, go to the TCP/IP option to locate the router’s IP address.
- In the browser, input the login credentials to access the router’s admin panel. Typically, these details can be found on the router’s back or its user manual. If you’ve misplaced the password, consider resetting the router.
- Post login, the router’s homepage will be displayed, listing all devices connected to your wireless network, usually under sections like Status or Wireless Client.
Automated Detection of Devices on a Wireless Network: For a more streamlined process of identifying devices on Wi-Fi, network scanning tools are engineered to offer detailed insights from wireless access points, encompassing SSID, device category, signal potency, and linked devices. These utilities are invaluable for device discovery and diagnosing security and performance challenges in large-scale wireless networks.
For instance, cyber adversaries often exploit weak points in enterprise wireless routers or access points to gain unauthorized access and control. They deploy tactics like packet interception, password theft, and middle-man attacks to exfiltrate confidential data.
Cutting-edge network scanning software can thwart unauthorized access by consistently monitoring and analyzing wireless devices for potential vulnerabilities.
Essential Features in Network Device Scanning Tools such as GEMS: Network scanning tools are crafted to simplify network monitoring, boasting features such as:
- Wi-Fi Heat-maps Creation: Contemporary tools can generate dynamic Wi-Fi heatmaps, enabling users to assess the potency and reach of specific access points. They also facilitate tracking of all linked and disconnected mobile devices via Wi-Fi access point polling.
- Port Scanning: These tools empower network administrators to detect and seal inactive WLAN ports, safeguarding against unauthorized access by potential threats.
- Unified Dashboard: These utilities offer a comprehensive view of the entire Wi-Fi framework. Network administrators can monitor metrics like device downtime, oversee wireless coverage, map network routes, and diagnose network challenges from a singular, modifiable dashboard using automation tools.
- Instant Alerts: Wireless monitoring tools can notify administrators about challenges like diminished signal strength and RF disruptions, which might cause network outages. Proactive monitoring can reduce network downtime and enhance operational efficiency.